Hackers linked to Russia came dangerously close to shutting down a dozen U.S. electric and gas plants in the early weeks of the Ukraine conflict, the CEO of a leading cybersecurity firm warned Tuesday.
According to Robert M. Lee, the founder and CEO of Dragos, a company that helps businesses respond to cyberattacks, hackers from a group called “Chernovite” were employing malicious software to try to knock down “around a dozen” U.S. electric and liquid natural gas sites.
“This is the closest we’ve ever been to having U.S. or European infrastructure, I’d say U.S. infrastructure, go offline,” Lee said in a briefing. “It wasn’t employed on one of its targets, they weren’t ready to pull the trigger, they were getting very close.”
Dragos collaborated with partners such as the Cybersecurity and Infrastructure Security Agency, the Department of Energy, the FBI, and the National Security Agency to “keep something off American soil that was going to be disruptive in nature,” according to Lee.
“I don’t use those words lightly, not trying to hype anything up, but the state actor responsible for this, there is no chance that this was not their go-to package to be able to actually bring down infrastructure,” Lee said.
PIPEDREAM
While the US government revealed last year that the new malware, known as PIPEDREAM, was capable of infecting US industrial control systems across various vital sectors, Lee’s statements suggest that the threat was more severe than officials had revealed. And his publication sheds new light on the vulnerability of the United States’ energy system to a crippling cyber attack — the potential of which sparked considerable anxiety in the run-up to Russian President Vladimir Putin’s February 2022 invasion.
Lee defined the malware as a “state-level, wartime capability.” He did not specify if the malware had been deployed in the targeted networks or if the hackers were merely on the verge of doing so.
While Dragos does not link hacker groups to nation governments as a matter of policy, several security researchers believe Chernovite’s PIPEDREAM virus is likely linked to Russia.
The United States disclosed the discovery of the hazardous malware in April 2022, just three weeks after President Joe Biden warned that Russia was “exploring alternatives for future cyberattacks” against the United States and urged critical infrastructure groups to beef up security.
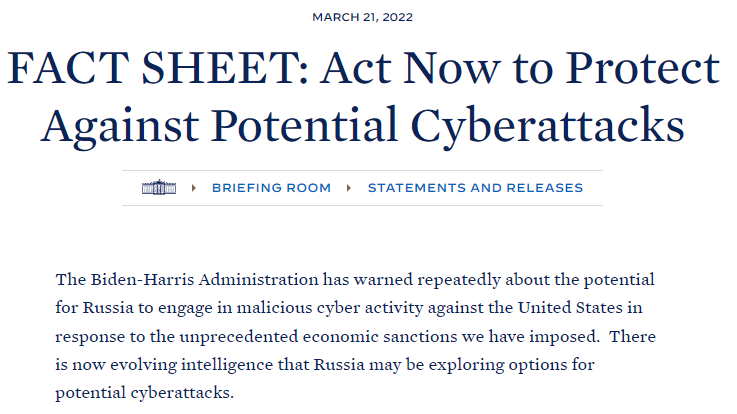
“I have previously warned about the potential that Russia could conduct malicious cyber activity against the United States, including as a response to the unprecedented economic costs we’ve imposed on Russia alongside our allies and partners,” Biden said in a statement at the time. “Today, my Administration is reiterating those warnings based on evolving intelligence that the Russian Government is exploring options for potential cyberattacks.”
PIPEDREAM malware is the “first ever” form that can be utilized across a wide range of industrial control systems and was not designed to disrupt a single system, making it very dangerous. The malware also does not enter computers via vulnerabilities that can be patched, making it extremely difficult to defend against.
“You could increase temperatures, you could have unsafe conditions in a plant,” Lee added. “There is no need to exploit anything, there is no need to find a vulnerability when a capability is already built into the plant so the plant environments can operate.”
Hack track record
Russian hackers pose serious threat to the security of a nation. Cyberattacks have targeted the websites of key German administrations, including enterprises and airports, according to the country’s Federal Cybersecurity Agency earlier this year. Killnet, a Russian hacker group, has claimed responsibility for the attack.
The same group also claimed responsibility for a cyber attack on NATO that disrupted connection with an airplane carrying disaster relief to Turkey and Syria.
“We are carrying out NATO strikes. Details in a closed channel,” the hacking gang, which aims to disrupt military and government websites in nations that back Ukraine, allegedly posted on one of its Telegram channels.
We have "cyberattack" on SAS yesterday (https://t.co/WgSQCTL496). Pro-russian, Killnet affiliated groups posing as muslims announcing attacks today against Swedish airports. Lufthansa experiencing a global outage (!) (thx @reiterberlin) -What's going on? https://t.co/mI80M38wXI pic.twitter.com/qm1vnoTd8n
— Henrik Moltke (@moltke) February 15, 2023
Meanwhile, hackers linked to a Russian bodybuilder and an IT professional attempted to hack into American nuclear research labs last year. The group, called Cold River, employed phishing techniques to gain access to the Brookhaven, Argonne, and Lawrence Livermore National Laboratories.
Cold River used email accounts to register domain names that resemble authentic links but route to a page created by the hacker. When a victim enters their information into the site, the hacker has access to it and can use it to access legitimate pages.
This isn’t the only Cold River hack. According to security researchers, the group registered domain names impersonating non-governmental organizations that probe Russian war crimes in 2022. Cold River published emails from a Proton account belonging to Richard Dearlove, the former head of the British intelligence service MI6 in May 2002. In 2016, the organization also targeted the British Foreign Office.
Information for this briefing was found via the Politico, Independent, Euronews, Vice, and the sources mentioned. The author has no securities or affiliations related to this organization. Not a recommendation to buy or sell. Always do additional research and consult a professional before purchasing a security. The author holds no licenses.